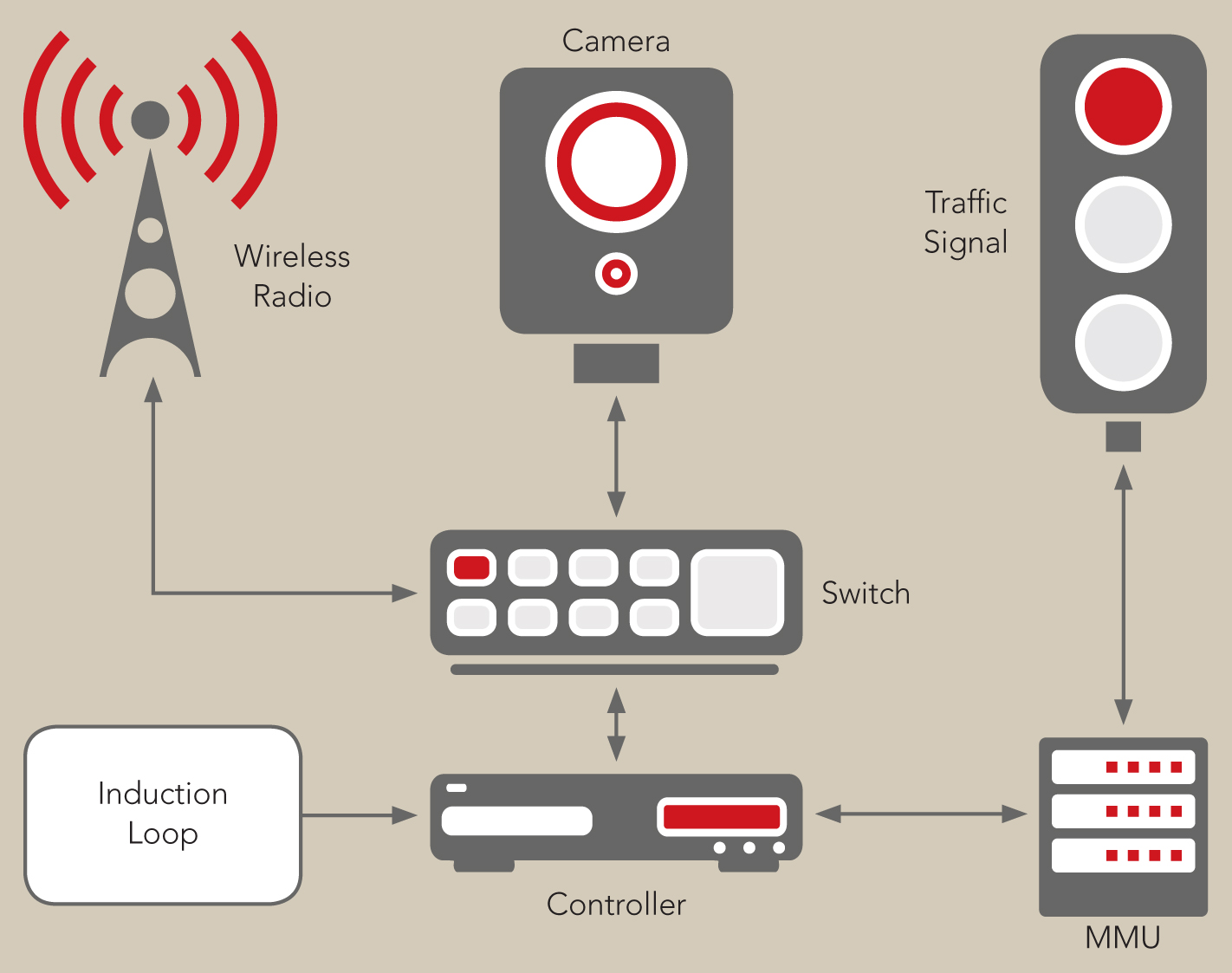
A schematic reveales how many potentially vunerable areas there are in a typical light installation.
This year’s ITS World Congress in Bordeaux will have three sessions dedicated to cyber security and the issue will also be addressed under connected and automated vehicles categories. Jon Masters finds out why.
American security researchers Charlie Miller and Chris Valasek attracted international press coverage recently when they demonstrated how they could hack into and take control of a vehicle from a remote laptop. While the implications are clearly serious for vehicle manufacturers, highway and transportation authorities also are being urged to sit up and consider the seriousness of cyber security threats.
Government IT networks are generally well guarded against malicious software or external hackers although the specific hardware and distributive nature of traffic control and ITS systems appear more vulnerable. Experts say cyber attacks on ITS and traffic management systems are likely, and authorities should act to address security weaknesses.
Delving deeper, the levels of threat and risk are mixed. Transportation departments in America are recording thousands of attempted internet-based cyber attacks every day - but virtually all are successfully blocked.
“There is a cyber-war under way,” says Doug Couto, independent IT security consultant and a former chief information officer for the Michigan State Government.
“Cyber attacks numbering in the region of 750,000 happen every day against the Michigan Government alone. There are vulnerabilities in traffic signals connected to the internet and risks associated with ITS software and hardware.
“When I was working for Michigan I could see all of this ITS technology being created and thought someone ought to pay more attention to built-in security. Systems are only as strong as their weakest link and people can find weaknesses and exploit them.”
Their report – ‘Green Lights Forever’ – showed it was easy to hack into a set of interconnected traffic signals via the communications network and the traffic signal controller. The report finds a general lack of security consciousness ‘in the entire field’ and concludes: ‘until these systems are designed with security as a priority, the entire traffic infrastructure will remain at risk’.
Allen Hillaker, one of the Michigan University researchers, says: “Up until now security has clearly not been a high priority in design of traffic control systems. In response to our report, the US Department of Transportation said the root cause was a ‘standards problem’.”
The specific standard is NTCIP 1202 which specifies communication protocols between traffic systems. “Standardisation should take security into account. When buying new equipment there is standard configuration but no security on top of that. There is not enough flexibility in the standard to allow for sufficient security up to now,” Hillaker says.
Existing standards are being updated and new cyber security standards are understood to be under development. This will take some time and in the meantime traffic signal systems are vulnerable to attack - although they are designed to fail-safe. “They go into fail-safe mode, overriding major errors. Any alteration of signal timings or settings would cause an annoyance rather than a safety issue,” says Hillaker.
Nonetheless, the study highlights possible weaknesses in hardware and communication networks and if ITS systems are vulnerable to attack at street level, could they allow hackers to infiltrate authorities’ central network control systems?
“Awareness of the issue is now a lot greater with the advent of V2V and V2X developments,” Hillaker says. “We are currently doing work to assess vehicle security, starting from within the vehicle, rather than from the outside looking in. However, a lot more thought is now going into V2X security.”
Potential weaknesses in ITS infrastructure are not generally considered as presenting high risks to transportation operations. A survey of attitudes towards cybersecurity among US transit and highway authorities for the National Cooperative Highway Research Programme indicates that while most authorities are aware of cyber security threats, most rank the risks as low or moderate. According to the survey, virtually none of the respondents were aware of any cyber attacks on their transportation control networks.
However, security breaches have occurred and the US Transportation Research Board has a number of related initiatives, including the hosting of a cyber security resource centre. This details a number of attacks on transportation systems, which have resulted in relatively minor consequences - thus far at least.
6666 WSP 4983 Parsons Brinckerhoff’s ITS security specialist Ryan Williams says: “Attacks do occur. State DOTs tell us that malignant attempts at finding ways into their IT systems via the internet or intranets commonly number in the thousands; but 99% are blocked,” he says.
“The issue with transport and specifically ITS infrastructure is that it’s not as sexy for targeting in comparison to airports or critical buildings. There is a lot of potential risk to ITS systems, however.
“It used to be acceptable to leave roadside hardware open to access, but the climate of threat has changed, partly because moves from analogue to digital communication potentially create access to whole networks if they are not adequately protected.”
NIST’s approach is intended to complement existing risk management practices, based on principles of identifying current status and assets to be protected, detection processes and response, and recovery plans.
“Transport authorities should be looking at where they are with regard to cyber security; identifying risks and developing protection measures and response plans, then reviewing these on an appropriate cycle. Cyber security is a fluid process,” Williams says.
Across in the UK, when Highways England was asked how it was addressing cyber security, it responded with the statement: “We take the security of our ITS infrastructure extremely seriously and have a central team in place to ensure our approach is joined up with our contractors.
“Where appropriate we follow guidance from the UK Centre for the Protection of National Infrastructure. We also have central guidelines for our contractors to follow on security and these are written into contracts where needed.”
International cooperation on cyber security is being stepped up and will be a theme at the 2015 ITS World Congress in Bordeaux. At least one technical committee of the international standards organisation, ISO/TC204, is known to be initiating work on the subject.
Information reported on the TRB’s resource centre makes clear that the US Department of Transportation (USDOT) is taking the issue very seriously. USDOT officials have pointed to problems caused by transportation’s insecure configuration of wireless networks, inadequate security of field equipment and poor practice in patching vulnerabilities. So far officials have played down the consequences of cyber attacks but have acknowledged the need for better ways of alerting all State DOTs to the issues and risks.
Cyber security experts are predicting that the Internet of Things, or any infrastructure networks linked to the internet, will present the biggest vulnerability due to the scale of the number of connected devices.
“The only perfect solution is to have zero connectivity, but we cannot have that,” Doug Couto says. “Systems are becoming more secure as awareness grows. Weaknesses still exist, but the industry is learning to assess the risks. Further training and awareness is needed, but the good news is that it’s happening.”
Hardware and network components
Alan Hayes, managing director of Ethernet equipment manufacturer and software supplier AMG, says cyber security needs to be a crucial part of the process when considering the choice of equipment supplier. This echoes long-running concerns about embedded ‘spyware’ in network equipment – especially when the equipment is supplied by overseas companies to potentially sensitive applications.
“Over the last few years we have seen many examples of state-sponsored surveillance and electronically-enabled industrial espionage, so these things do happen. It may not be that any particular network is being targeted but if spyware were to be embedded in certain types of equipment, it could then monitor the system from the inside finding a ‘way out’ to the internet. This would, in turn, inform a third party of a ‘way in’ which is a lot easier that just trying to break in to an otherwise secure network from the outside.”
He also emphasises how purchasing policies could have an impact on cyber security.
“Authorities compelled to go for the lowest price are exposed to covert subsidence by those with malicious intent in order to undercut the competition and ensure their indoctrinated products are installed. So authorities need to be certain about exactly where the components they are buying are designed and manufactured and the source of the embedded firmware – which is not easy given the current extent of rebranding products,” he says.
He ends with some advice: “If you can’t visit the facility where your network equipment is designed and manufactured, and inspect the software it contains, then you have to question how far it can be trusted.”
Cyber security starts with design
According to491 TRL’s Alan Stevens and Peter Vermaat, the increasing digital nature and complexity of connected and automated vehicles will inevitably prove increasingly attractive targets for ‘hackers’ trying to discover and exploit security weaknesses. The research agency is advising a number of clients on safety and security issues raised by connected and automated vehicles.
Recent high-profile cybersecurity incidents include:
• Cloning of digital ignition keys allowing vehicles to be stolen
• Remote control of a Jeep from a laptop by exploiting its Infrastructure-to-Vehicle connectivity
• Vulnerability of the Onstar RemoteLink app allowing unauthorised location of a GM vehicle, door unlock and remote start
• Demonstration of access to safety-critical vehicle systems through spoofing a DAB radio station to access the vehicle’s systems.
While these security flaws have mostly concerned vehicle manufacturers, they highlight concerns about the potential for security lapses in connected and automated vehicles to have serious safety consequences for road users and national infrastructures (such as vehicle-borne Improvised Explosive Devices).
Although these demonstrations of cyber security weaknesses have prompted public debate and concern among technology providers, total security is unachievable and needs to be proportionate to the risk. Security by design is easier and cheaper than remedial measures and so greater efforts are likely to focus on early incorporation of security in the design process. A good example is the need for security researchers to dismantle the dashboard of a Tesla Model S and decompile the firmware before they could begin hacking into the system. The researchers found the system was well designed and was easily patched once the weaknesses had been identified.
Threat vectors
A number of key ‘threat vectors’ can be described for ITS systems, according to WSP Parsons Brinckerhoff security specialist Ryan Williams. He describes the threat vector of ‘cyber enabled physical attacks’, such as remote disabling of CCTV cameras or security systems. Such attacks are rare, but the risk should still be addressed, he says.
Beyond internet-based cyber attacks, physical attacks can be perpetrated through direct connection to hardware, or via remote access to networks and control systems. “I have observed countless opportunities for people to plug laptops into hardware ports and from there gain access to networks, controllers and electronic signs,” Williams says.
“The simple answer to this is lock roadside cabinets and install tamper alarms; don’t label control equipment because this is effectively the keys to accessing the network; lock down unused ports and don’t use default factory passwords. Power over Ethernet consumption can be monitored as well to ensure any malignant intent can be spotted.”
The use of ‘Honeypots’ is another protection against remote network access. These create fake IP addresses to alert attacks to host organisations. Data diodes can be installed as well to control flow of data, Williams says.
‘Conventional’ internet-based cyber attacks from IP addresses can be prevented by firewalls or by creating a ‘demilitarized zone’ – a safe area for testing against malware, viruses or trojans. Additionally, Bastion Hosts provide a way of communicating ‘patches’ of data while maintaining a physical disconnection between an authority’s home network and the internet.
“Separate networks can be created and access control implemented fairly simply with lists of safe IP addresses,” Williams says. “Deep packet inspection can be carried out if unauthorised access is suspected, but this needs careful consideration and regulatory control of what’s being done, because it involves looking deep into the data coming in. This is generally only recommended if the threat is raised to a high level, needing a forensic degree of investigation.”
Protection measures against ‘cyber enabled physical attacks’ include Security Event Management – an electronic map of alarms in the overall control system. “It’s possible to have too many alarms, so it’s advisable to automate a response to certain types of attack that’s appropriate to the threat level,” Williams says.
“Software is available that learns what is ‘normal’ in terms of communication and assets on the network and then shuts out anything that is abnormal. This works well for transportation systems because their networks are fairly static. Anything that changes can be identified as malignant.”
American security researchers Charlie Miller and Chris Valasek attracted international press coverage recently when they demonstrated how they could hack into and take control of a vehicle from a remote laptop. While the implications are clearly serious for vehicle manufacturers, highway and transportation authorities also are being urged to sit up and consider the seriousness of cyber security threats.
Government IT networks are generally well guarded against malicious software or external hackers although the specific hardware and distributive nature of traffic control and ITS systems appear more vulnerable. Experts say cyber attacks on ITS and traffic management systems are likely, and authorities should act to address security weaknesses.
Delving deeper, the levels of threat and risk are mixed. Transportation departments in America are recording thousands of attempted internet-based cyber attacks every day - but virtually all are successfully blocked.
“There is a cyber-war under way,” says Doug Couto, independent IT security consultant and a former chief information officer for the Michigan State Government.
“Cyber attacks numbering in the region of 750,000 happen every day against the Michigan Government alone. There are vulnerabilities in traffic signals connected to the internet and risks associated with ITS software and hardware.
“When I was working for Michigan I could see all of this ITS technology being created and thought someone ought to pay more attention to built-in security. Systems are only as strong as their weakest link and people can find weaknesses and exploit them.”
Signals hacked
In 2014, researchers from the University of Michigan’s electrical engineering and computer science department published a study into the network security of traffic signals.Their report – ‘Green Lights Forever’ – showed it was easy to hack into a set of interconnected traffic signals via the communications network and the traffic signal controller. The report finds a general lack of security consciousness ‘in the entire field’ and concludes: ‘until these systems are designed with security as a priority, the entire traffic infrastructure will remain at risk’.
Allen Hillaker, one of the Michigan University researchers, says: “Up until now security has clearly not been a high priority in design of traffic control systems. In response to our report, the US Department of Transportation said the root cause was a ‘standards problem’.”
The specific standard is NTCIP 1202 which specifies communication protocols between traffic systems. “Standardisation should take security into account. When buying new equipment there is standard configuration but no security on top of that. There is not enough flexibility in the standard to allow for sufficient security up to now,” Hillaker says.
Existing standards are being updated and new cyber security standards are understood to be under development. This will take some time and in the meantime traffic signal systems are vulnerable to attack - although they are designed to fail-safe. “They go into fail-safe mode, overriding major errors. Any alteration of signal timings or settings would cause an annoyance rather than a safety issue,” says Hillaker.
Nonetheless, the study highlights possible weaknesses in hardware and communication networks and if ITS systems are vulnerable to attack at street level, could they allow hackers to infiltrate authorities’ central network control systems?
Implications
The problem Miller and Valasek identified was related to communication connections between an Android smartphone and Fiat Chrysler’s in-vehicle entertainment systems (security issues have also been discovered with other manufacturers’ vehicles). So could ITS architecture present a weak spot in the security of vehicle to infrastructure technology?“Awareness of the issue is now a lot greater with the advent of V2V and V2X developments,” Hillaker says. “We are currently doing work to assess vehicle security, starting from within the vehicle, rather than from the outside looking in. However, a lot more thought is now going into V2X security.”
Potential weaknesses in ITS infrastructure are not generally considered as presenting high risks to transportation operations. A survey of attitudes towards cybersecurity among US transit and highway authorities for the National Cooperative Highway Research Programme indicates that while most authorities are aware of cyber security threats, most rank the risks as low or moderate. According to the survey, virtually none of the respondents were aware of any cyber attacks on their transportation control networks.
However, security breaches have occurred and the US Transportation Research Board has a number of related initiatives, including the hosting of a cyber security resource centre. This details a number of attacks on transportation systems, which have resulted in relatively minor consequences - thus far at least.
“The issue with transport and specifically ITS infrastructure is that it’s not as sexy for targeting in comparison to airports or critical buildings. There is a lot of potential risk to ITS systems, however.
“It used to be acceptable to leave roadside hardware open to access, but the climate of threat has changed, partly because moves from analogue to digital communication potentially create access to whole networks if they are not adequately protected.”
Cyber security framework
Initial advice for US authorities is to adopt the cyber security framework developed by NIST, the National Institute of Standards & Technology. The framework was developed to be technology neutral following a 2013 US Presidential Executive Order on ‘Improving Critical Infrastructure Cybersecurity’.NIST’s approach is intended to complement existing risk management practices, based on principles of identifying current status and assets to be protected, detection processes and response, and recovery plans.
“Transport authorities should be looking at where they are with regard to cyber security; identifying risks and developing protection measures and response plans, then reviewing these on an appropriate cycle. Cyber security is a fluid process,” Williams says.
Across in the UK, when Highways England was asked how it was addressing cyber security, it responded with the statement: “We take the security of our ITS infrastructure extremely seriously and have a central team in place to ensure our approach is joined up with our contractors.
“Where appropriate we follow guidance from the UK Centre for the Protection of National Infrastructure. We also have central guidelines for our contractors to follow on security and these are written into contracts where needed.”
International cooperation on cyber security is being stepped up and will be a theme at the 2015 ITS World Congress in Bordeaux. At least one technical committee of the international standards organisation, ISO/TC204, is known to be initiating work on the subject.
Information reported on the TRB’s resource centre makes clear that the US Department of Transportation (USDOT) is taking the issue very seriously. USDOT officials have pointed to problems caused by transportation’s insecure configuration of wireless networks, inadequate security of field equipment and poor practice in patching vulnerabilities. So far officials have played down the consequences of cyber attacks but have acknowledged the need for better ways of alerting all State DOTs to the issues and risks.
Cyber security experts are predicting that the Internet of Things, or any infrastructure networks linked to the internet, will present the biggest vulnerability due to the scale of the number of connected devices.
“The only perfect solution is to have zero connectivity, but we cannot have that,” Doug Couto says. “Systems are becoming more secure as awareness grows. Weaknesses still exist, but the industry is learning to assess the risks. Further training and awareness is needed, but the good news is that it’s happening.”
Hardware and network components
Alan Hayes, managing director of Ethernet equipment manufacturer and software supplier AMG, says cyber security needs to be a crucial part of the process when considering the choice of equipment supplier. This echoes long-running concerns about embedded ‘spyware’ in network equipment – especially when the equipment is supplied by overseas companies to potentially sensitive applications.
“Over the last few years we have seen many examples of state-sponsored surveillance and electronically-enabled industrial espionage, so these things do happen. It may not be that any particular network is being targeted but if spyware were to be embedded in certain types of equipment, it could then monitor the system from the inside finding a ‘way out’ to the internet. This would, in turn, inform a third party of a ‘way in’ which is a lot easier that just trying to break in to an otherwise secure network from the outside.”
He also emphasises how purchasing policies could have an impact on cyber security.
“Authorities compelled to go for the lowest price are exposed to covert subsidence by those with malicious intent in order to undercut the competition and ensure their indoctrinated products are installed. So authorities need to be certain about exactly where the components they are buying are designed and manufactured and the source of the embedded firmware – which is not easy given the current extent of rebranding products,” he says.
He ends with some advice: “If you can’t visit the facility where your network equipment is designed and manufactured, and inspect the software it contains, then you have to question how far it can be trusted.”
Cyber security starts with design
According to
Recent high-profile cybersecurity incidents include:
• Cloning of digital ignition keys allowing vehicles to be stolen
• Remote control of a Jeep from a laptop by exploiting its Infrastructure-to-Vehicle connectivity
• Vulnerability of the Onstar RemoteLink app allowing unauthorised location of a GM vehicle, door unlock and remote start
• Demonstration of access to safety-critical vehicle systems through spoofing a DAB radio station to access the vehicle’s systems.
While these security flaws have mostly concerned vehicle manufacturers, they highlight concerns about the potential for security lapses in connected and automated vehicles to have serious safety consequences for road users and national infrastructures (such as vehicle-borne Improvised Explosive Devices).
Although these demonstrations of cyber security weaknesses have prompted public debate and concern among technology providers, total security is unachievable and needs to be proportionate to the risk. Security by design is easier and cheaper than remedial measures and so greater efforts are likely to focus on early incorporation of security in the design process. A good example is the need for security researchers to dismantle the dashboard of a Tesla Model S and decompile the firmware before they could begin hacking into the system. The researchers found the system was well designed and was easily patched once the weaknesses had been identified.
Threat vectors
A number of key ‘threat vectors’ can be described for ITS systems, according to WSP Parsons Brinckerhoff security specialist Ryan Williams. He describes the threat vector of ‘cyber enabled physical attacks’, such as remote disabling of CCTV cameras or security systems. Such attacks are rare, but the risk should still be addressed, he says.
Beyond internet-based cyber attacks, physical attacks can be perpetrated through direct connection to hardware, or via remote access to networks and control systems. “I have observed countless opportunities for people to plug laptops into hardware ports and from there gain access to networks, controllers and electronic signs,” Williams says.
“The simple answer to this is lock roadside cabinets and install tamper alarms; don’t label control equipment because this is effectively the keys to accessing the network; lock down unused ports and don’t use default factory passwords. Power over Ethernet consumption can be monitored as well to ensure any malignant intent can be spotted.”
The use of ‘Honeypots’ is another protection against remote network access. These create fake IP addresses to alert attacks to host organisations. Data diodes can be installed as well to control flow of data, Williams says.
‘Conventional’ internet-based cyber attacks from IP addresses can be prevented by firewalls or by creating a ‘demilitarized zone’ – a safe area for testing against malware, viruses or trojans. Additionally, Bastion Hosts provide a way of communicating ‘patches’ of data while maintaining a physical disconnection between an authority’s home network and the internet.
“Separate networks can be created and access control implemented fairly simply with lists of safe IP addresses,” Williams says. “Deep packet inspection can be carried out if unauthorised access is suspected, but this needs careful consideration and regulatory control of what’s being done, because it involves looking deep into the data coming in. This is generally only recommended if the threat is raised to a high level, needing a forensic degree of investigation.”
Protection measures against ‘cyber enabled physical attacks’ include Security Event Management – an electronic map of alarms in the overall control system. “It’s possible to have too many alarms, so it’s advisable to automate a response to certain types of attack that’s appropriate to the threat level,” Williams says.
“Software is available that learns what is ‘normal’ in terms of communication and assets on the network and then shuts out anything that is abnormal. This works well for transportation systems because their networks are fairly static. Anything that changes can be identified as malignant.”














