Transport staff using the Context-Aware system.
David Crawford looks at new developments in security for wireless communications networks.
Wireless communications - including mobile phone links - are well recognised as a key transport technology. They are low-cost, easily installed, well supported by the wider IT industry and offer the protocols of choice for much metropolitan area networking on which transport applications can piggyback.Unsurprisingly, their emergence is being paralleled by concerns over security, privacy and smart payment vulnerabilities. Secure exchange of information over Wireless LANs (WLANs) has long been a major concern of IT departments round the globe, not least in public transport where the physical infrastructure of access points may be shared between public and internal users (see Sidebar, "Mobilising the mobile workforce").
Terrorism has added another dimension. The response has been a flurry of activity around the world.
In the US, for example, the Texas-based Wi-Fi Alliance has recently expanded its Wi-Fi Protected Access (WPA2) enterprise security protocol support, to increase numbers of Extensible Authentication Protocols (EAPs) supported in security certification testing.
Further incremental improvements are now in progress. In September 2009, the Alliance is releasing a new White Paper on The State of Wi-Fi Security.
But, says Frank Provenzano of California-based traffic management technology company
A specific area of concern is dynamic message signs, whose vulnerability to 'wireless hacks' has become increasingly apparent in 2009.
Says Provenzano: "Today, there is a broad requirement for transportation network communications infrastructure and information to be shared between agencies and the driving public. But public agencies often do not appreciate the compromises they make in security when they deploy these systems."
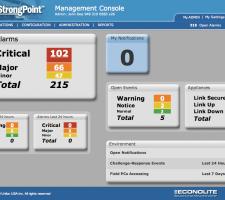
In response, Econolite and partner company Uniloc have developed StrongPoint, launched at the November 2008
Meanwhile, in the transit sector, the American Public Transport Association is starting a one-year project on developing security application standards for communications. It is drawing on the experience in dealing with vulnerabilities of the country's public utilities.
Director of Technical Services Lou Sanders told ITS International: "We have in membership a number of consultancies bridging both sectors. Their knowledge is proving invaluable."
Europe
European initiatives currently under way include the European Commission (EC)-supported PRECIOSA (PRivacy Enabled Capability In co-Operative Systems and safety Applications) project, focussing on co-operative systems covering wireless vehicle-to-vehicle (V2V), vehicle-to infrastructure (V2I) and vehicle-to-X (V2X) communications. It is highlighting perceived contradictions between meaningful observation of traffic patterns and the need for individual privacy.Another EC-supported project, SeVeCom (Secure Vehicular Communication), is addressing the security and privacy of future vehicle communication networks. Its main areas of focus are: threats (such as bogus information, denial of service or identity cheating); requirements for (for example) authentication, availability and privacy; and operational properties, including network scale, privacy, cost and trust.
Meanwhile, EC Data Protection Supervisor (EDPS) Peter Hustinx has commented on perceived gaps in the EC's ITS Action Plan, scheduled for adoption by end-2009. He has called for greater clarification on the specific circumstances in which a vehicle will be tracked, strict limits on use of location devices and assurances that location data are not disclosed to unauthorised recipients.
In the UK, the UTMC (Urban Traffic Management and Control) service has commissioned international consultants
Early research contributed to technical specifications and standards including a mandatory requirement for each UTMC project to prepare its own security policy, based on BS (British Standard) 7799:1999. (This has now achieved global standard status as the ISO 27000 series of information security standards, the first of which have now been published).
UTMC allows ITS applications in urban traffic management to communicate and share information using a central database, via wired and (increasingly) wireless links. Some 70 UK local authorities currently operate UTMC systems while international deployments include Port Elizabeth in South Africa (host country for the 2010 FIFA World Cup); Sharjah, in the UAE: and the Chilean capital of Santiago, site of one of the largest SCOOT deployments in the world.
Middle Eastern traffic agencies routinely cite UTMC in their specifications. The current security review will, therefore, have international benefits.
UTMC Ltd Director Mark Cartwright: "As is implicit in the UTMC philosophy, wireless communications can be used across a range of transport sectors with varying security concerns. Applications include control of signalised intersections via junction-wide radio LAN; management of transport-related sites such as car parks or bus depots, dissemination of travel information, for example real-time journey time predictions or disruption alerts on display screens; downloading from CCTV arrays, on-street and in-vehicle, for security and vehicle crime reduction; links with in-vehicle equipment, such as for DSRC-based electronic fee collection, or downloading fuel management data; and the coming area of ad-hoc vehicle networks."
Secure confidentiality is important for personal information (including that carried in CCTV images, such as licence plate details, and the subscriber details held on toll tags) under the European Convention on Human Rights, which looks to protect individual privacy. For traffic signal control and transport site management, integrity and availability are the main considerations, to avoid both malicious disruption and loss of service - either of which can affect safety.
In travel information, the issues are primarily availability and accuracy - lack of which can prejudice public confidence in advisory systems and, hence, modal shift. Authentication is universally important.
The current study will produce security guidelines based on experience with operational UTMC systems, building on a 2007 internal review. This urged major updates in the areas of CCTV, tolling (specifically its financial components) and traveller information displays.
It also highlighted the risks of open networking protocols potentially allowing accidental or malicious impacts from outside the system, justifying appropriate emphasis on encryption (now built into most relevant components), access rights, firewalling and audit.
Among initiatives by European companies, Netherlands-headquartered